The vulnerable exposed systems that are unmonitored and facing the internet, are the most attacked system for the attackers nowadays.
According to a research done by The Institution of Electronics and Telecommunication Engineers (IETE) and CyberPeace Foundation (CPF) along with Autobot Infosec Private Limited, nearly 51 million attack events have been recorded between April to December 2021 on the Data Centres Network-based Threat Intelligence sensors network specifically simulated in India.
The Institution of Electronics and Telecommunication Engineers (IETE) and CyberPeace Foundation (CPF) along with Autobot Infosec Private Limited have jointly deployed Threat Intelligence sensor networks to capture and examine the behavioral techniques of threat actors.
The study is a part of CyberPeace Foundation’s e-Kawach programme to implement a comprehensive public network and threat intelligence sensors across the country in order to capture internet traffic and analyse the real-time cyber attacks that a location or an organisation faces. A credible intelligence on real-time threats empowers organisations or a Country to build CyberSecurity policies, according to a NewsVoir report.
The objective of this research was to examine the different types of signatures that can be used as exhibitors of compromise on the simulated Data centre network by collecting information that can mitigate future attacks on real networks.
“By deploying the simulated network we can collect data on patterns of attack, the different types of attack vector for the different protocols and the recent trends of malicious activity,” a spokesperson of CyberPeace Foundation said.
Trends noticed by the research
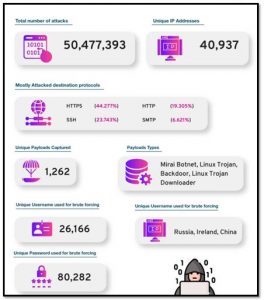
Data collection for the current study started from April 2021 to December 2021. It was found that during the aforementioned time span the deployed network instance captured a total number of 50,477,393 attack events from a total number of 40937 Unique IP addresses globally. Mostly Attacked destination protocols were:
- HTTPS (44.277%)
- SSH (23.743%)
- HTTP (19.305%)
- SMTP (6.621%)
Advisory
Do not expose services like SSH, HTTP, HTTPS, SMTP, SMB, MSSQL, MYSQL unnecessarily to the internet and maintain a strong Password Policy by using a strong password for all devices and online accounts. The passwords should be at least 8-13 characters long and should contain at least one upper case (A-Z), numeric character (0-9), and a special character (!@% & ….). Do not use the same password for all your online accounts. All the passwords should be different for different accounts and try avoiding a password that consists in the dictionary. The network firewalls should always be patched with the latest security updates. Add the attacker IP addresses mentioned in the report to the blacklist of the firewall solution in order to block inbound connections from the respective IP addresses.






